As with IOS I am presenting the Route Reflector setup between 3 Juniper routers (Olive).
The setup is almost the same, but I am going to cover the configuration in slightly more detail, as familiarity with IOS appears to be more common. This assumes that the Juniper boxes have already been configured with hostnames and root passwords.
Here is the topology I am using:
1. Configure IP addressing (RR as example)
I always configure the loopback address first. Many routing protocols rely on this.
# set interfaces lo0 unit 0 family inet address 1.3.3.7/32
# set interfaces em0 unit 0 family inet address 10.12.0.1/24
# set interfaces em1 unit 0 family inet address 10.13.0.1/24
(Aside: an easy way to pull these commands after they have been configured is
# run show configuration interfaces lo0.0 | display set
)
2. Set up routing autonomous system
In this case we are working with iBGP so all three routers will be within the same AS
# set routing-options autonomous-system 503
3. Configure the BGP group
Groups allow Junos to logically bunch settings together. Much like the peer-group in IOS. I chose the name IBGP to reflect the work we will be doing. I also like to use all-caps when defining names in Junos as it is easier for me to recognize.
# edit protocols bgp group IBGP
(Another bonus with Junos is all variable names are tab completable:
# edit protocols bgp group ?
Possible completions:
Group name
IBGP Group name
Cool huh?)
4. Edit BGP group settings
Here we set the AS of the peers, their IP addresses and other things like policies :)
Note: usually we would peer using loopback addresses for redundancy. In most production designs redundant connections would allow multiple IGP paths to lo0.0. That is not the case in this example.
RR:
[edit protocols bgp group IBGP]
# set peer-as 503
# set type internal
# set neighbor 10.12.0.2
# set neighbor 10.13.0.3
# commit
R2:
[edit protocols bgp group IBGP]
# set peer-as 503
# set type internal
# set neighbor 10.12.0.1
# commit
R3:
[edit protocols bgp group IBGP]
# set peer-as 503
# set type internal
# set neighbor 10.13.0.1
# commit
5. Stand by and allow BGP to come up (30s or so). Verify:
# run show bgp summary
Groups: 1 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0 0 0 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.12.0.2 503 3 3 0 2 0 0/0/0/0 0/0/0/0
10.13.0.3 503 3 2 0 2 0 0/0/0/0 0/0/0/0
See if you can notice something odd with this output
5. Check routing table on the RR:
# run show route protocol bgp
inet.0: 5 destinations, 5 routes (5 active, 0 holddown, 0 hidden)
No routes?
The default behavior of Junos is to accept all NLRIs advertised from peers, but not to advertise any prefixes unless they are specified in an export policy.
6. Define an export policy to send all connected routes:
Policies can be very complex, so I am going to create a very simple one named IBGP:
# edit policy-options policy-statement IBGP
[edit policy-options policy-statement IBGP]
# set policy-options policy-statement IBGP from protocol direct
# set policy-options policy-statement IBGP then accept
This takes all prefixes that are directly connected and places them in the BGP Adjacency-RIB-out for advertisement.
7. Apply the policy to the BGP group
# top edit protocols bgp group IBGP
[edit protocols bgp group IBGP]
# set protocols bgp group IBGP export IBGP
# top commit
8. Verify that prefixes are being seen by the routers
# run show bgp summary
Groups: 1 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0 4 2 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.12.0.2 503 22 22 0 2 8:23 1/2/2/0 0/0/0/0
10.13.0.3 503 22 21 0 2 8:23 1/2/2/0 0/0/0/0
And check the routing table on the RR:
# run show route protocol bgp
inet.0: 7 destinations, 9 routes (7 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
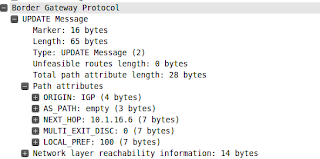
2.3.3.7/32 *[BGP/170] 00:05:04, localpref 100
AS path: I
> to 10.13.0.3 via em1.0
3.3.3.7/32 *[BGP/170] 00:05:04, localpref 100
AS path: I
> to 10.12.0.2 via em0.0
10.12.0.0/24 [BGP/170] 00:05:04, localpref 100
AS path: I
> to 10.12.0.2 via em0.0
10.13.0.0/24 [BGP/170] 00:05:04, localpref 100
AS path: I
> to 10.13.0.3 via em1.0
Looks good....right?
Remember that pesky split horizon rule of iBGP? Let's check the routing table on one of the spoke routers for the loopback address of the other spoke (3.3.3.7/32):
# run show route 2.3.3.7
[edit]
Apparently reflection is not running. This can also be seen from the full BGP neighbor output:
# run show bgp neighbor | match cluster
[edit]
Nothing. All we have to do to fix this is turn on router-reflection on the hub router. In IOS we would define each peer or peer-group as being a route-reflector-client. In juniper the idea is similar, but we set a cluster ID on the desires route reflector(s):
# edit protocols bgp group IBGP
[edit protocols bgp group IBGP]
# set cluster 7.3.3.1
[edit protocols bgp group IBGP]
# commit
commit complete
And let's check the full BGP neighbor output:
# run show bgp neighbor | match cluster
This should allow the spokes to see each other's loopback prefix:
# run show route 2.3.3.7
inet.0: 6 destinations, 7 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
2.3.3.7/32 *[BGP/170] 00:01:04, localpref 100
AS path: I
> to 10.12.0.1 via em0.0
And the other spoke:
# run show route 3.3.3.7
inet.0: 6 destinations, 7 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
3.3.3.7/32 *[BGP/170] 00:01:38, localpref 100
AS path: I
> to 10.13.0.1 via em0.0
To recap, here are the configs:
RR# show | display set | except "version|system"
set interfaces em0 unit 0 family inet address 10.12.0.1/24
set interfaces em1 unit 0 family inet address 10.13.0.1/24
set interfaces lo0 unit 0 family inet address 1.3.3.7/32
set protocols bgp group IBGP type internal
set protocols bgp group IBGP export IBGP
set protocols bgp group IBGP cluster 7.3.3.1
set protocols bgp group IBGP peer-as 503
set protocols bgp group IBGP neighbor 10.12.0.2
set protocols bgp group IBGP neighbor 10.13.0.3
set policy-options policy-statement IBGP from protocol direct
set policy-options policy-statement IBGP then accept
R3# show | display set | except "version|system"
set interfaces em0 unit 0 family inet address 10.12.0.2/24
set interfaces lo0 unit 0 family inet address 3.3.3.7/32
set protocols bgp group IBGP type internal
set protocols bgp group IBGP export IBGP
set protocols bgp group IBGP peer-as 503
set protocols bgp group IBGP neighbor 10.12.0.1
set policy-options policy-statement IBGP from protocol direct
set policy-options policy-statement IBGP then accept
R3# show | display set | except "version|system"
set interfaces em0 unit 0 family inet address 10.13.0.3/24
set interfaces lo0 unit 0 family inet address 2.3.3.7/32
set protocols bgp group IBGP type internal
set protocols bgp group IBGP export IBGP
set protocols bgp group IBGP peer-as 503
set protocols bgp group IBGP neighbor 10.13.0.1
set policy-options policy-statement IBGP from protocol direct
set policy-options policy-statement IBGP then accept
That's all for now. Please ask any questions you may have.
/m